Enhanced Security Role Configuration (ACM 8.0 and later)
Configuring Users
User objects can be created by clicking the Add, Other and User menu items. The new User object will be created in the folder selected. Double click on new User object to edit the General tab. Enter a descriptive name for this user object. A Description is optional. It is enabled by default*.
Select the User tab. Enter a Domain\Username or Domain\Groupname that corresponds to a Windows account being used by this user.
Examples:
- CompanyXYZDomain\SCADAAdmins (Windows AD group)
- CompanyXYZDomain\MeasurementUsersGroup (Windows AD group)
- CompanyXYZDomain\jsmith (Windows AD user)
- LocalMachineName\jsmith (individual local user account)
Lastly, click the ellipsis button next to the Role name and Add or Select a Role to assign to this user. Click the Save disc to complete the User configuration.
Configuring Roles
Role objects can be created by clicking the Add, Other and Role menu items. The new Role object will be created in the folder selected. Double click on the new Role object to edit the General tab. Enter a descriptive name for this role object. A Description is optional.
Tip
Modify, Create and Delete are each considered separate privileges in ACM.
Role Tab
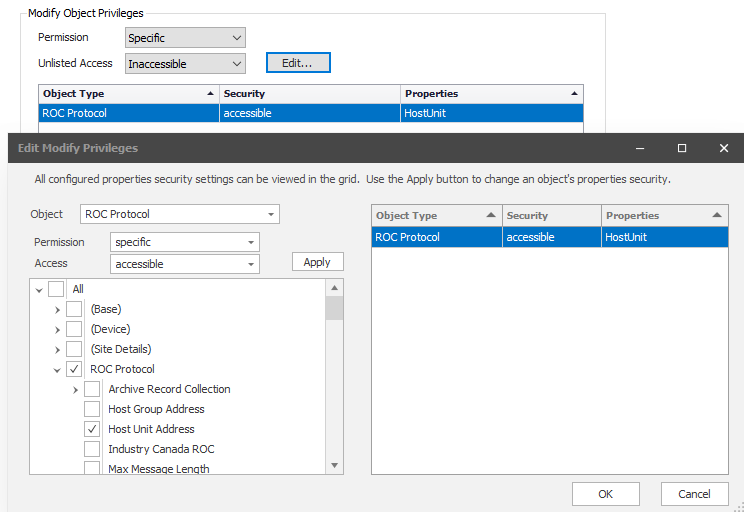
Modify Object Privileges
| Permission Option | Description |
|---|---|
All | Users can modify any property of any type of object. |
| None | Users cannot modify any property of any type of object. |
Specific | Users can modify specific properties of specific object types. Select any desired object types and properties and define them as accessible or inaccessible. You can mark some object types to be fully configurable, some to be entirely un-configurable, and others to have specific properties that are configurable. Unlisted Access: You can then configure whether the rest of the properties (those not listed in your selection) are accessible or inaccessible. |
Moving Objects
A special note on moving objects (considered modification) to different folders in the configuration - To move an object, you must have Modify privilege for the ParentId property.
Create Object Privileges
| Permission Option | Description |
|---|---|
| All | Users can create any type of object. |
| None | Users cannot create any type of object. |
| Specific | Users can create specific object types. Select any desired object types, and then define whether the list represents object types that can be created (accessible) or cannot be created (inaccessible). |
Delete Object Privileges
| Permission Option | Description |
|---|---|
| All | Users can delete any type of object. |
| None | Users cannot delete any type of object. |
| Specific | Users can delete specific object types. Select any desired object types, and then define whether the list represents object types that can be deleted (accessible) or cannot be deleted (inaccessible). |
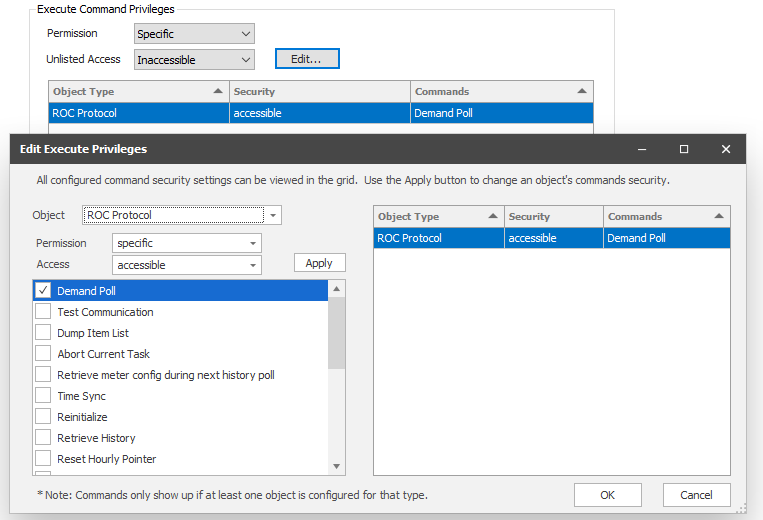
Execute Command Privileges
| Permission Option | Description |
|---|---|
| All | Users can execute any command on any type of object. |
| None | Users cannot execute any command on any type of object. |
| Specific | Users can execute specific commands on specific object types. Select any desired object types and commands, and then define whether the rest of the commands (those not listed in your selection) are accessible or inaccessible. Note: Only object types present in the configuration (at least one instance) will expose the commands for selection here. |
Security Note
When security is enabled, only the Role option to Configure Security determines whether security objects can be created, deleted or modified - even if security objects are selected as part of the 'specific' list of objects.
Configure Security
The Configure Security privilege allows users to create/modify/delete User and Role objects as well as enable/disable security. Note also that if the $Server property "Windows administrators have full access" property is enabled, members of the Windows Administrators group will also be able to configure all objects including security objects.
Click the Save disc to complete the Role configuration
Simplifying the Security Configuration
You can simplify your configuration by making use of the Access setting. If most of the properties on a given object type will be accessible, then select only those properties that should be inaccessible and set Access to 'Inaccessible'. The reverse is also true – if most of the properties will be inaccessible, then select only the properties that will be accessible and set the Access to 'Accessible'.
Also, if only a few object types will require limited configuration access, then set the 'Unlisted Access' (on the previous form) to 'Accessible' and limit the access to only the objects and properties that require specific permissions.
Configuring Folder Overrides
Folder overrides can be managed by right-clicking on the folder in the Tree View and selecting Edit. The Folder object will be opened. Select Security Overrides and Edit Overrides. Each record has a User and a Role object to assign. When a Role object is paired with a User object in the folder override settings, ACM will use the permissions configured in the paired Role object to determine whether actions can be performed on objects within the folder and in child folders. Permissions outside of the folder will still use the Role object assigned directly to the User object.
Once the desired changes are made close the records dialog and Click the Save disc to complete the Folder Override configuration.
Use Case: The Operator Role
In this example we will assume we have a user with a domain or local machine account named Operator. Consider the following server-wide security object configuration in ACM:
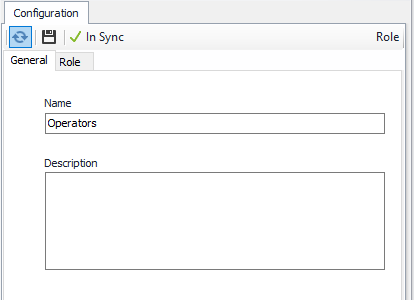
Role Object
General Tab
Name = Operators
Role Tab
Modify only the 'HOSTUnit' property of ROC Protocol objects.
Unlisted Access = Inaccessible. In this case no other properties can be modified by this Role.
Create/Delete could be set to none if this role should not create or delete objects.
Execute the 'Demand' command on all ROC protocol device objects.
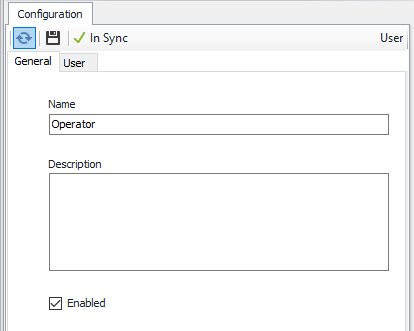
User Object
General Tab
Name = Operator
User Tab
Username = Operator (Domain/Workgroup Account)
Role = Operators
In this case with security ENABLED this user would be able to do the following:
- Modify only the 'HOSTUnit' property on any ROC Protocol object. No other configuration changes could be made.
- Execute the 'Demand' command on all ROC protocol device objects in the configuration.
- This user would NOT be able to configure security in any folder.
- This user would NOT be able to create or delete ANY objects in ANY folder.
In this case with security DISABLED this user would be able to do the following:
- Modify/Create/Delete all objects in any folder, including security-related objects.
- Execute Commands against all objects in any folder, including security-related objects.
For assistance, please submit a ticket via our Support Portal, email autosol.support@autosoln.com or call 281.286.6017 to speak to a support team member.