Recommended Configuration Steps
General Tab
See the General Object Configuration page.
Overview
The Role object is one part of the ACM security configuration. When user security is enabled (by enabling the option in the $Server object), the User objects and Role objects work together to define which user or group accounts can connect to ACM, which configuration changes they are allowed to make and which commands they're allowed to execute.
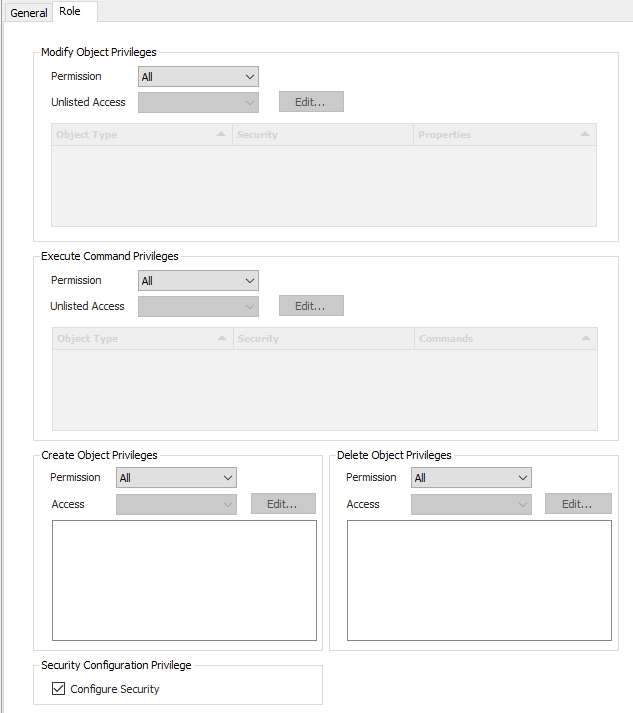
Role Tab
Modify Object Privileges
Use this section to control whether user's of the role have permission to make changes to the selected object types and properties. The permissions can be setup to allow access to specific properties and deny the rest, or to deny access to specific properties and allow the rest.
Execute Command Privileges
Use this section to control whether user's of the role have permission to execute commands on the selected object types. The permissions can be setup to allow access to specific commands and deny the rest, or to deny access to specific commands and allow the rest.
Create Object Privileges
Use this section to control whether user's of the role have permission to create specific types of objects. The permissions can be setup to allow creation of specific object types and deny the rest, or to deny creation of specific object types and allow the rest.
Delete Object Privileges
Use this section to control whether user's of the role have permission to delete specific types of objects. The permissions can be setup to allow deletion of specific object types and deny the rest, or to deny deletion of specific object types and allow the rest.