ACM requires a properly configured MQTT broker and TLS certificates for MQTT publishing to function. It is highly advisable to take these steps before continuing ACM Monitor TLS setup:
Work with a qualified security professional to determine the best means of securing MQTT communications for your use case. AUTOSOL support cannot provide security advice.
Configure the MQTT broker according to your needs. Note: ACM requires use of a TLS certificate.
Test using a third party MQTT client with support for certificates and Sparkplug B. AUTOSOL used Node-RED during testing, among others.
Certificate configuration in particular tends to be the most problematic area of MQTT setup. Taking these steps, with the help of a qualified security professional, will greatly simplify ACM configuration.
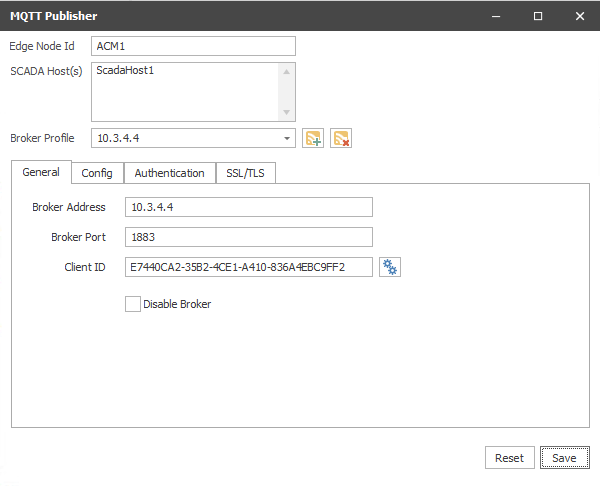
General Tab
After the MQTT Publisher form opens, click the “plus” button ()to add a new profile with your requirements.
ACM publishes data via MQTT according to the Sparkplug B specification. As such the MQTT topic structure will follow the following format: namespace/group_id/message_type/edge_node_id/[device_id]
For example, the topic spBv1.0/ACM/DDATA/ACM1/ROC1234 would be broken down as follows:
spBv1.0 - Indicates that the message topic & payload conforms to the Sparkplug B specification.
ACM - The group id - a means of logically grouping edge nodes, by geographical area or business unit, for example. For the 9.1 release of ACM, this will always be “ACM”.
DDATA - The message type - a “device data” message in this case.
ACM1 - The Edge node id (description below)
ROC1234 - The device object name from the ACM configuration.
Edge Node Id
The Sparkplug B identifier ACM will use for itself when publishing. Using the example above (spBv1.0/ACM/DDATA/ACM1/ROC1234), "ACM1" is the portion configured by this setting. This gives an identifier to a specific instance of ACM and should be unique from other edge nodes (including other ACM installations) that may be publishing to the same broker(s).
SCADA Hosts(s)
Defines the scada_host_id to which ACM will subscribe for STATE updates (the SCADA Host going OFFLINE, for example). If there are multiple SCADA Hosts, enter each host ID on a separate line. For more information on Scada Hosts, see the Sparkplug B Specification. Note: This should be kept as short as possible as it adds to the size of every message sent to the broker.
Broker Address
The IP address of the broker. This can be entered in both IPv4 or IPv6 format.
ACM will attempt to connect to the first enabled broker listed. If it is unable to make that connection, or the connection is later lost, ACM will continue through the enabled broker list in a round-robin fashion.
Client ID
The MQTT identifier for a client connecting to an MQTT broker. This must be unique from other clients sharing the same broker(s), including other ACM installations. By default, it is auto generated but can also be manually updated to something more human readable. A new, random client ID can be generated by clicking the "cog" button ( ) to the right of the client ID box.
Disable Broker
Allows you to setup the broker properties but prevent ACM from connecting to that broker.
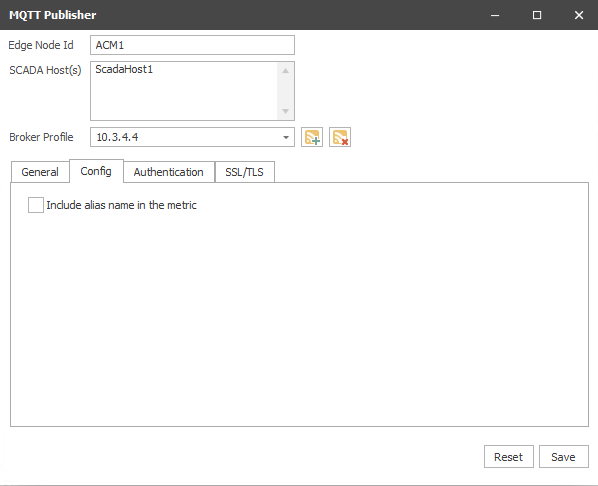
Config Tab
The "Include alias name in the metric" setting provides the ability include the alias name in the metric. When unchecked, only the alias number is included in the payload instead of the full tag name. This option is helpful for troubleshooting but will increase bandwidth used per message.
Authentication Tab
The Authentication tab properties allow entry of username and password, if authentication is required by the broker.
SSL/TLS Tab
ACM currently provides supports three categories of TLS certificates:
CA signed Server Certificate - when using a public certificate authority
CA Certificate file - when using a private certificate authority
Self Signed Certificates
1. CA Signed Server Certificate
Use the CA signed server certificate option when there is already a CA signed certificate uploaded server side (broker) and the same cert is used for client authentication. There is no need to upload a certificate here.
2. CA Certificate file
The CA certificate used in server side (broker) should be used here and must be in PEM format. Intermediate certificates can also be used here but they must be combined into a single bundle in PEM format.
3. Self Signed Certificates
This option is used when both client & server require mutual authentication. The client certificate must be signed by the same CA certificate as the broker. The CA file must be in PEM format. The client certificate file combined with its key file must be uploaded in PFX format. The passphrase can also be given if the client certificate is password protected.
After setting up all the properties related to the broker, click “Save” to apply the settings. The process can be repeated for additional brokers.