Starting the Server
Select the Status icon in the ACM Monitor app.
Start the asiData service if not already running.
Enable the property checkbox for ‘Show Optional Services’.
Select asiOPCUA then click the Start Services button.
Optionally, you can start the Server using the Windows Services app. The service is named Autosol OPC UA Service.
Configuring the Server
The Server is configured using the ACM Monitor app. The first time the Server is started or the first time it is configured, a default configuration file is automatically created.
The configuration file asiOpcUa.Config.xml should not be edited directly without consultation from AUTOSOL support staff. Refer to Appendix B.
Start the ACM Monitor app, select the Client Protocols icon then click the OPC UA Configure button. This will show the server configuration dialog.
Properties Tab
Button | Function |
Save | Saves changes and writes new values to configuration file. Certain changes will require the Server to be stopped and restarted to take effect. |
Cancel | Discards any changes and exits dialog. |
Reset | Resets all controls to their default value. |
| Setting | Purpose |
Reject SHA1 Signed Certificates | Select this option to reject SHA1 signed client certificates and require only SHA256 certificates. Default - not selected. |
Accept Non-Secure Sessions | Select this option to allow client applications to connect a session without using encryption – Security Policy None. Default - not selected. |
Accept Untrusted Certificates | Select this option to accept untrusted certificates from clients. This option should only be enabled for troubleshooting purposes and disabled during production run time. Default - not selected. |
Allow Writes to Items by Anonymous Users | Select this option to allow anonymously connected users to write to items (Nodes) in the address space. Default - not selected. |
Send Complete Certificate Chain | Select this option to allow the Server to send the complete certificate chain during a session connection. Default - not selected. |
Add Application Certificate to Trusted Store | Select this option to automatically copy the AUTOSOL OPC UA server self-signed certificate to the trusted store. Default - not selected. |
Register With Local Discovery Service | Select this option if an OPC UA Local Discovery Service is running and the Server should register with it upon startup. Default - not selected. |
Enable Diagnostics | Select this option to enable the collection of the Server’s diagnostic and throughput data. Default - not selected. |
Minimum Certificate Key Size | The minimum certificate key strength that will be accepted. Default - 1024 |
Session Nonce Length | The length of nonce to use in the CreateSession service. Default – 32 |
Log Option - Errors | Select this option to log error messages to the ACM logger. Default - not selected. |
Log Option - Warning | Select this option to log warning messages to the ACM logger. Default - not selected. |
Log Option - Trace | Select this option to log verbose informational messages to the ACM logger. Default - not selected. |
Log Option – OPC UA Stack | Select this option to log message from underlying OPC UA stack to the ACM logger. Default - not selected. |
Service Port – opc.tcp | TCP port to listen on for client opc.tcp connections. Default - 5337 |
Service Port - https | TCP port to listen on for client https connections. Default - 6337 |
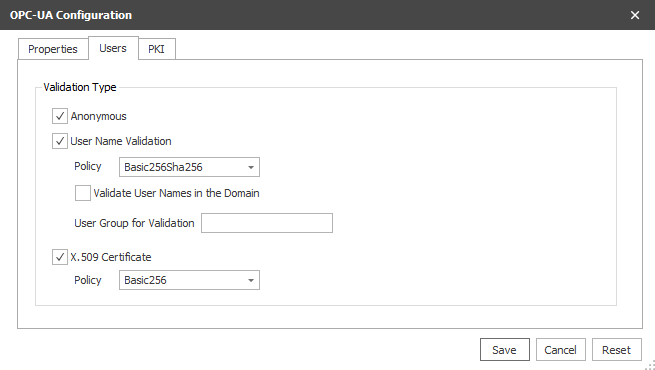
Users Tab
| Setting | Purpose |
Anonymous | Select this option to allow anonymous user connections. Default - selected. |
User Name Validation | Select this option to allow username and password connections. Username and password will be validated by Windows. Default - selected. |
User Name Policy | Select the encryption policy to use to pass log on information |
Validate User Names in the Domain | Select this option to validate username and passwords, and optionally user groups, in the network domain. Deselect to validate username and password, and optionally user groups, on the local machine account. |
User Group for Validation | The user group that the supplied user must be a member of in order to be validated. Leave blank to not validate against a user group. Location of the group is determined by the Validate User Names in the Domain property. |
X.509 Certificate | Select this option to validate users by trusted certificate. Default - selected. |
X.509 Certificate Policy | Select the encryption policy to use to pass user certificate information |
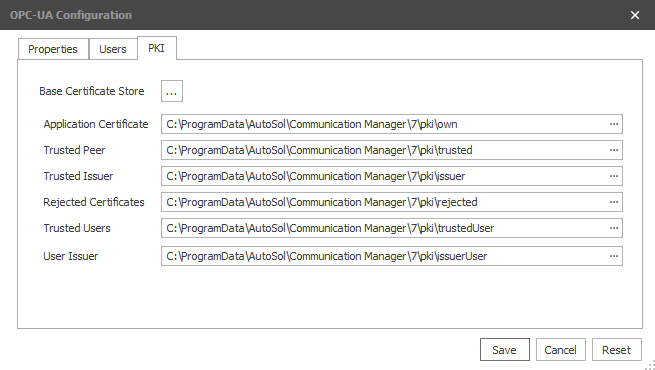
PKI Tab
| Setting | Purpose |
Base Certificate Store | Shows the folder selection dialog to select the base folder path of the pki certificate store. Once selected, all the path edit boxes will be updated to the base folder path. |
Application Certificate | Location of the OPC UA Server instance certificate. If the “Add Application Certificate to Trusted Store” property is enabled on the properties tab, a self-signed certificate will be generated and stored here. |
Trusted Peer | The location used to store the trusted UA client application instance certificates. This store will contain the public key certificates of the trusted application instances. |
Trusted Issuer | Location of peer certificate authority, if required. |
Rejected Certificates | Location the Server will move rejected certificates to. |
Trusted Users | The location used to store the trusted UA application user certificates. This store will contain the public key certificates of the trusted user instances. |
User Issuer | Location of user certificate authority, if required. |