...
| Table of Contents | ||||||||
|---|---|---|---|---|---|---|---|---|
|
| Info |
|---|
While MQTT Publishing can occur without using a secure connection, AUTOSOL suggests using TLS certificates for MQTT publishing to functionin all production environments. It is highly advisable to take these steps before continuing ACM Monitor TLS setup:
Certificate configuration in particular tends to be the most problematic area of MQTT setup. Taking these steps, with the help of a qualified security professional, will greatly simplify ACM configuration. |
...
General Tab
After the MQTT Publisher form opens, click the “plus” button ()to add a new profile with your requirements.
...
The Authentication tab properties allow entry of username and password, if authentication is required by the broker.
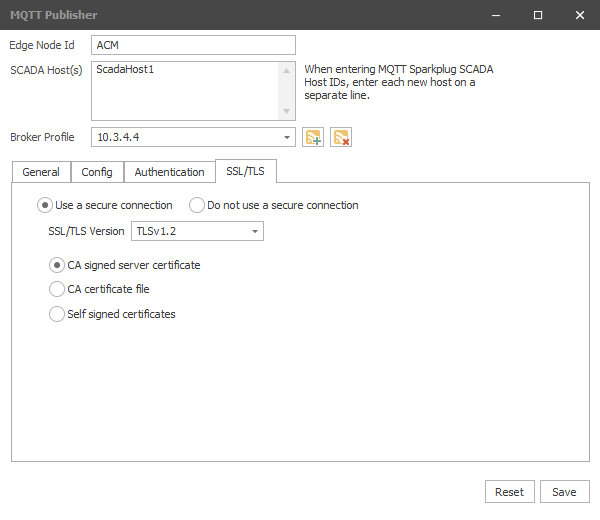
SSL/TLS Tab
Secure Connections
By default, the Use a secure connection is selected enabling configuration of SSL/TLS options. For non-production environments, the Do not use a secure connection option can be used for testing.
ACM currently provides supports three categories of TLS certificates:
...
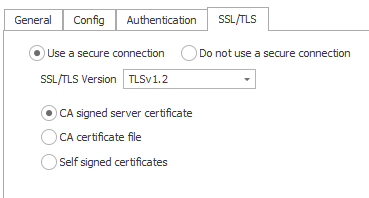
1. CA Signed Server Certificate
Use the CA signed server certificate option when there is already a CA signed certificate uploaded server side (broker) and the same cert is used for client authentication. There is no need to upload a certificate here.
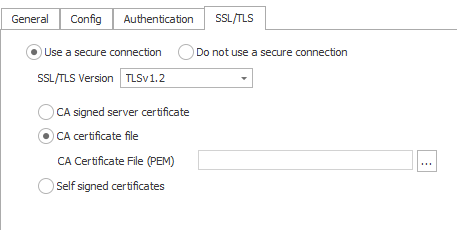
2. CA Certificate file
The CA certificate used in server side (broker) should be used here and must be in PEM format. Intermediate certificates can also be used here but they must be combined into a single bundle in PEM format.
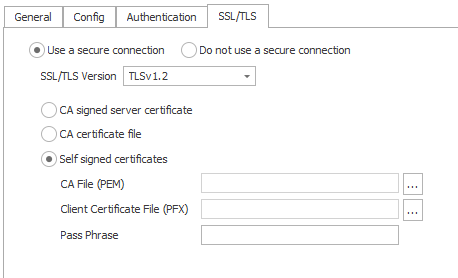
3. Self Signed Certificates
This option is used when both client & server require mutual authentication. The client certificate must be signed by the same CA certificate as the broker. The CA file must be in PEM format. The client certificate file combined with its key file must be uploaded in PFX format. The passphrase can also be given if the client certificate is password protected.
...